02. How to execute sos Report Command? Written on . Posted in sos command.
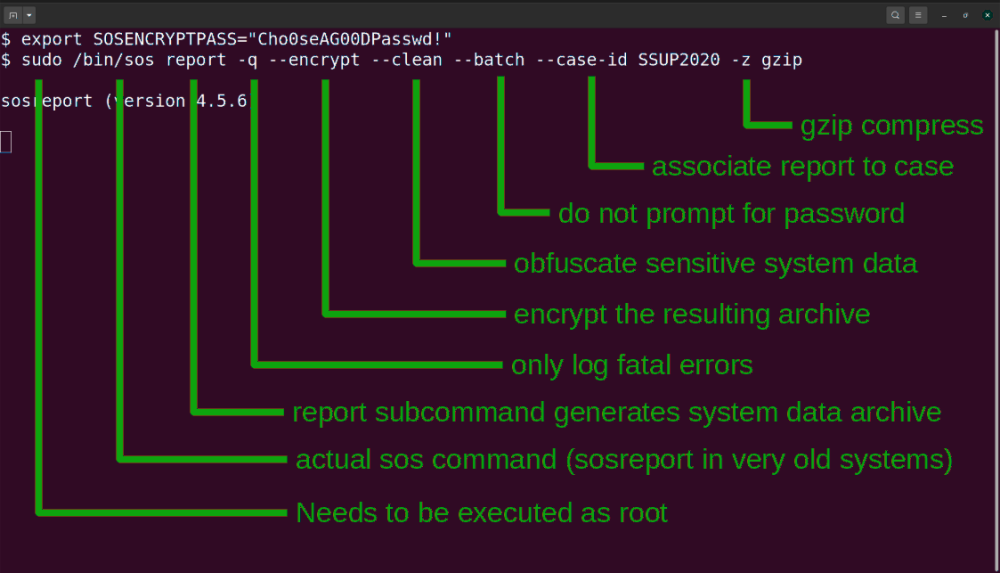
- --encrypt: Encrypt the resulting archive, and determine the method by which that encryption is done by either a user prompt or environment variables.
- --encrypt-pass: Encrypts the resulting archive that sosreport produces using GPG. The provided PASS for symmetric encryption
- --clean: This function is designed to obfuscate potentially sensitive information from an sos report archive in a consistent and reproducible manner.
- --label LABEL: Specify an arbitrary identifier to associate with the archive. Labels will be appended after the system's short hostname and may contain alphanumeric characters.
- --case-id NUMBER: Specify a case identifier to associate with the archive. Identifiers may include alphanumeric characters, commas and periods ('.').
Finishing plugins [Running: logs]
Finished running plugins
Creating compressed archive...
Your sosreport has been generated and saved in:
/tmp/sosreport-ganymede-SUPP-0001-2024-10-01-xgsjkdb.tar.xz
Size 11.87MiB
Owner root
sha256 de66aa92c59f179af7ce0906056a58e8360772b56bbcbaed2f935bc9c009ee75
Please send this file to your support representative.
Finishing plugins [Running: logs]
Finished running plugins
Found 1 total reports to obfuscate, processing up to 4 concurrently
sosreport-ganymede-SUPP-0001-2024-10-01-euofqva : Beginning obfuscation...
sosreport-ganymede-SUPP-0001-2024-10-01-euofqva : Obfuscation completed [removed 88 unprocessable files]
Successfully obfuscated 1 report(s)
Creating compressed archive...
A mapping of obfuscated elements is available at
/tmp/sosreport-host0-SUPP-0001-2024-10-01-euofqva-private_map
Your sosreport has been generated and saved in:
/tmp/sosreport-host0-SUPP-0001-2024-10-01-euofqva-obfuscated.tar.xz
Size 11.14MiB
Owner root
sha256 3d8c1efa5f4b241469a32b4807d3210d58fb971731d785e13501257c468105ee
Please send this file to your support representative.
Finishing plugins [Running: logs]
Finished running plugins
Creating compressed archive...
Your sosreport has been generated and saved in:
/tmp/secured-sosreport-ganymede-SUPP-0001-2024-10-01-plyzuet.tar.xz.gpg
Size 11.90MiB
Owner root
sha256 01bd4e339e6823235c36f6ef044d0d60e0243d80bda65f333fca31ce2dd8e894
Please send this file to your support representative.
Finishing plugins [Running: logs]
Finished running plugins
Found 1 total reports to obfuscate, processing up to 4 concurrently
sosreport-ganymede-alabel-SUPP-0001-2024-10-01-iwormbj : Beginning obfuscation...
sosreport-ganymede-alabel-SUPP-0001-2024-10-01-iwormbj : Obfuscation completed [removed 88 unprocessable files]
Successfully obfuscated 1 report(s)
Creating compressed archive...
A mapping of obfuscated elements is available at
/tmp/sosreport-host0-alabel-SUPP-0001-2024-10-01-iwormbj-private_map
Your sosreport has been generated and saved in:
/tmp/secured-sosreport-host0-alabel-SUPP-0001-2024-10-01-iwormbj-obfuscated.tar.xz.gpg
Size 11.20MiB
Owner root
sha256 743902e923340381d5d559b90bdbf336a4d5e98701d19c233006e7825a9298ec
Please send this file to your support representative.
/etc/sos/sos.conf file, and then just run sos report. Here’s an example:$ egrep -v "^#|^$" /etc/sos/sos.conf
[global]
batch = yes
[report]
enable-plugins = sar
all-logs = yes
[collect]
[clean]
keywords = SecretApp
[plugin_options]
sar.all_sar=on
Conclusion
sosreport offers a wide range of options that make it a powerful tool for system diagnostics and support. From collecting logs and configuration files to running plugin-based checks across major subsystems, its flexibility makes it ideal for troubleshooting complex issues. Whether you're generating a standard report, limiting data collection to specific plugins, or running it in batch mode, there’s likely a set of options that fits your workflow. Don’t hesitate to explore commands like --only-plugins, --log-level, or --batch to tailor reports to your needs—you’ll be surprised how much useful information you can uncover.
analysing analyzing sos-report sos report sosreport analysis diagnotic troubleshooting Linux tool
